CodeScene can provide SSO using a generic OAuth2 integration that can be used with any OAuth2 provider that supports the Authorization Code flow. The CodeScene configuration page for this contains default settings for a few common providers. OKTA is not one of them, but this article will give you some guidance for configuring OKTA integration.
- First, make sure you have set the CodeScene Host URL properly:

- You must then define a CodeScene app on your OKTA organization and assign it to the users/groups you want to make available for mapping to roles in CodeScene. More information on this can be found here.
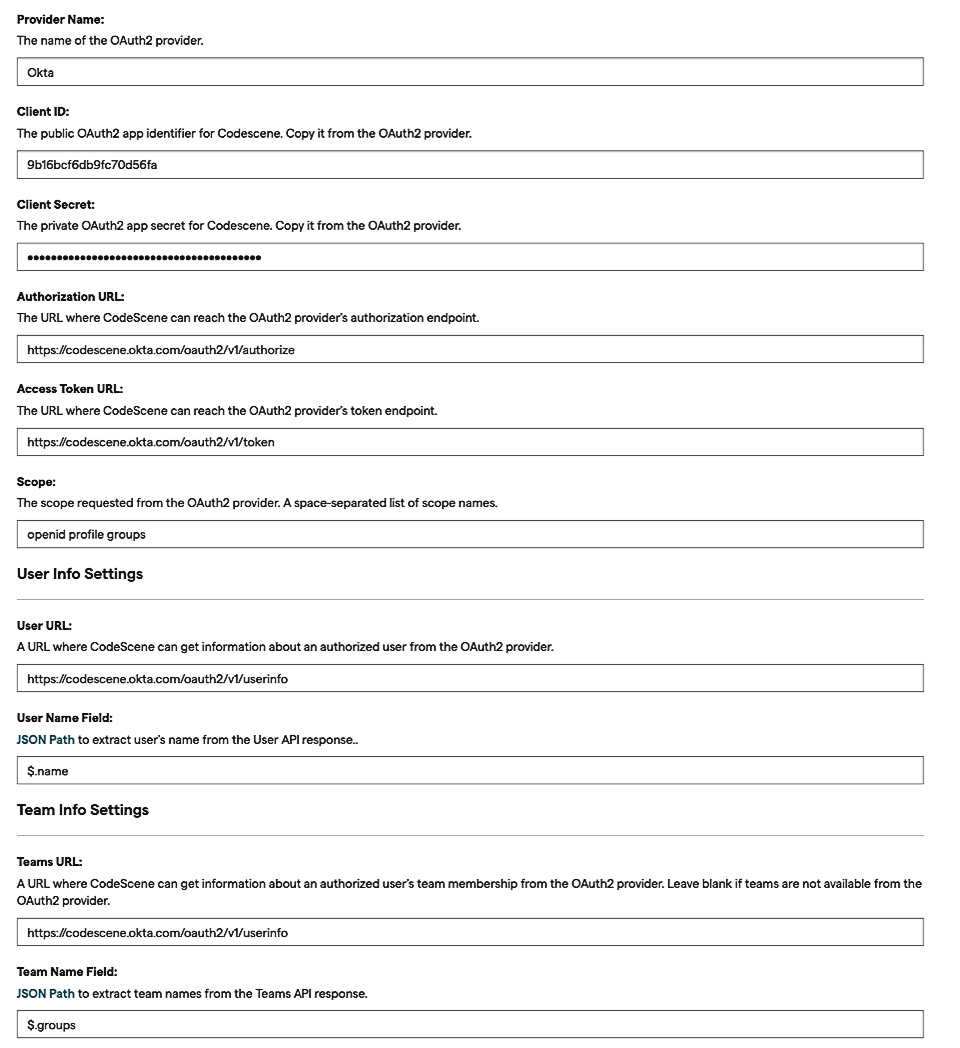
- You now use the Client ID and Secret from the app you created on OKTA, set URLs that CodeScene will connect to according to the OKTA API specification, and set Scope and User/Team Field Path like this:
4. If everything works correctly, OKTA users should now be able to log in to CodeScene.
5. You can then give required access to OKTA users by assigning CodeScene roles to OKTA users or groups on the root, group, or project level.
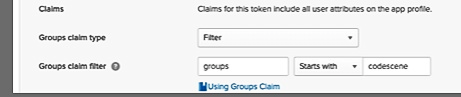
A common source of problems when doing the OKTA configuration has been making the user groups available to CodeScene on OKTA. Adding Groups claim filter should resolve this.
Although OKTA side configuration is outside the scope of CodeScene support, we are happy to assist if you still experience issues after following the steps above.
